What is PCI Compliance? 12 Requirements and How to Secure Your Payment Environment
- 18 min read
PCI compliance ensures safe handling of cardholder data.
With this article you’ll learn everything about PCI compliance, from its various levels to becoming PCI compliant to the risk of non-compliance and more.

Last year, the global average data breach cost was $4.45 million USD.
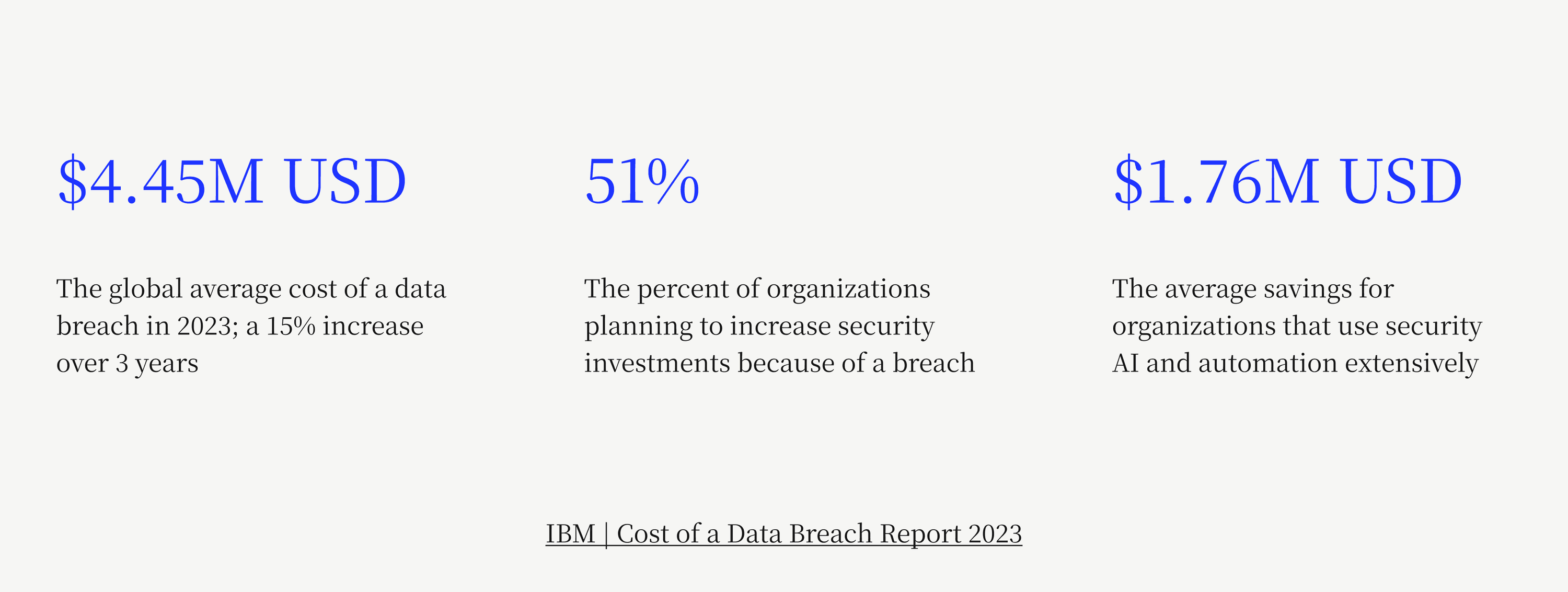
As these incidents become increasingly commonplace, it’s important for organizations—particularly merchants with e-commerce operations that interact with sensitive payment information—not to get complacent when it comes to their security measures. Finance teams especially have a part to play in keeping their customers’ data safe, as stewards of the company’s payment flows.
Data breaches take many shapes, with sensitive payment information—like cardholder data—often being exposed. While it’s impossible to guarantee that your business will never fall victim to a breach, by adhering to PCI compliance requirements and following a PCI compliance checklist, you can minimize the likelihood that it will happen.
When it comes to handling customers’ credit card information, the Payment Card Industry Security Standards Council (PCI SSC) has established rules that businesses must follow to ensure basic protection for consumers and minimize chances of fraud or breaches occurring within the payment ecosystem.
With this guide, you’ll learn what it means to be PCI compliant, how to become PCI compliant, and how to maintain payment security compliance. Plus, you’ll see how Versapay’s payment processing software helps you securely accept payments.
Table of contents
What is PCI compliance?
PCI compliance refers to whether a merchant adheres to the technical and operational requirements established by the PCI SSC to ensure safe handling of cardholder data. PCI compliance focuses on three core elements of merchants’ business:
1) How merchants obtain and handle sensitive credit card data from their customers—and how those details are collected and securely transmitted.
2) How merchants securely store credit card data, including their processes for encrypting, monitoring, and testing access to credit card data.
3) How merchants continuously monitor and ensure security controls—forms, questionnaires, vulnerability scanning services, audits, etc.—are in place.
1. How merchants obtain and handle credit card data:
To ensure the highest level of security, it’s best if customers’ payment information never touches your servers. Using a PCI compliant third-party payment processing software that securely tokenizes customers’ payment information (meaning the data is turned into a random string of characters so that it can’t be viewed) is a great way to minimize your contact with sensitive data.
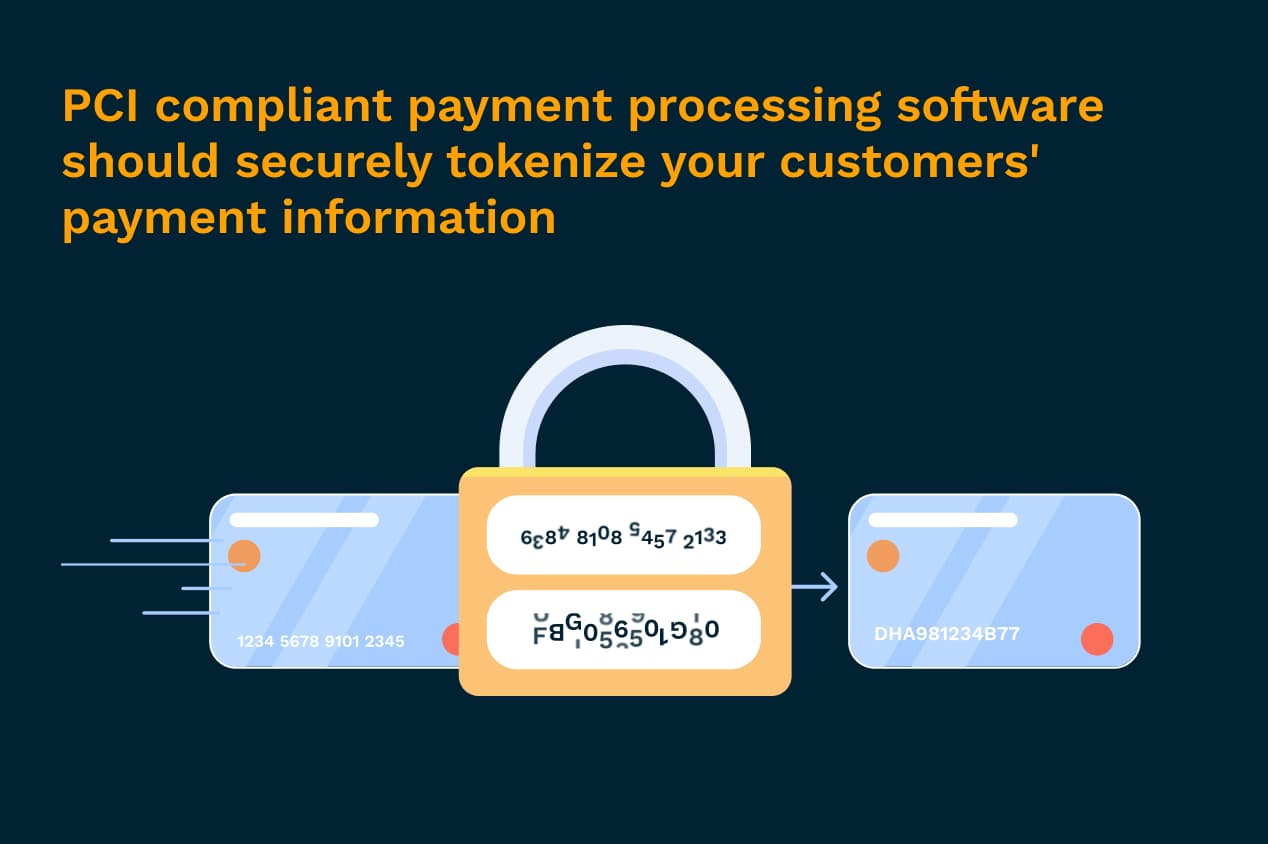
2. How merchants store credit card data:
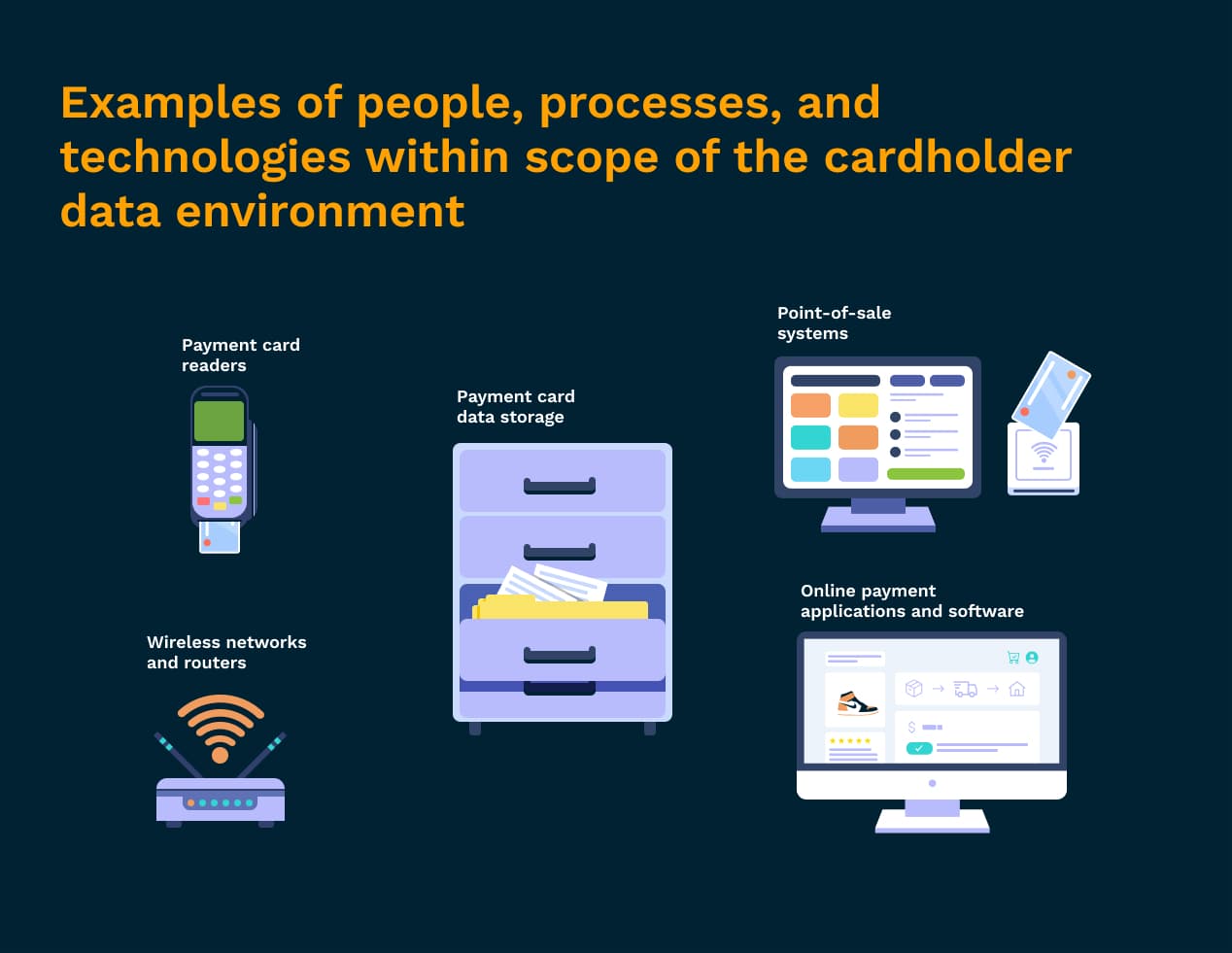
The goal of the PCI Data Security Standards is to minimize the scope of the cardholder data environment. This means that all the people, processes, and technologies that store, process, or transmit credit card information have been pared down to only those most vital to facilitating transactions.
Anything that comes into contact with cardholder data at any point is considered in-scope for PCI compliance. Because anything within the payment ecosystem that touches cardholder data must be confirmed as compliant with PCI guidelines, it’s in your best interest to limit which people, devices, and systems have access to sensitive cardholder or authentication information for the sheer benefit of making things easier on your team.
Here are some examples of what’s considered in-scope for PCI compliance:
The card readers you use to accept in-person payments
Your point of sale systems
Any networks or wireless access routers used to send payment information
Anywhere payment card data is stored or transmitted (includes paper-based records)
Applications and software used to accept payments online
3. How merchants continuously monitor security controls:
PCI compliance is an ongoing effort, requiring businesses to give evidence that they’re meeting required security protocols annually. It’s important to understand that security is not a one and done process. Systems need to be continuously monitored for potential vulnerabilities, and as cyber threats continue to evolve so should your defense methods.
What is the PCI Security Standards Council?
The PCI SSC was established in 2006 when five of the major credit card brands—Visa, Mastercard, American Express, Discover, and Japan Credit Bureau—came together to create global standards for how companies should manage credit card data. Prior to this, each of the card brands kept their own separate sets of requirements.
The PCI Data Security Standards (PCI DSS) are the rules established to govern how businesses manage cardholder data to ensure secure payment processing. These are updated every three years. Rather than the PCI SSC, it’s the card brands and acquiring banks who handle enforcing PCI compliance.
As of this article’s publication date, the most recent version of the standards is PCI DSS v4.0. This version looks to:
Meet the evolving security needs of the payment industry
Promote security as a continuous process
Add flexibility for different methodologies
Enhance validation methods
Who does PCI DSS apply to?
If your business receives income from cards—debit, credit, prepaid, etc.—you are responsible for PCI compliance. Even if everything is outsourced.
Official PCI Security Standards Council response: The PCI Data Security Standard (PCI DSS) applies to all entities that store, process, and/or transmit cardholder data. It covers technical and operational practices for system components included in or connected to environments with cardholder data. If you accept or process payment cards, PCI DSS applies to you.
What are the 4 PCI compliance levels?
There are varying PCI compliance levels (with Level 1 being the most stringent and Levels 2 to 4 having fewer requirements) based on factors like the volume of credit card transactions your business processes annually. Here’s a breakdown of what each of these PCI compliance levels means:
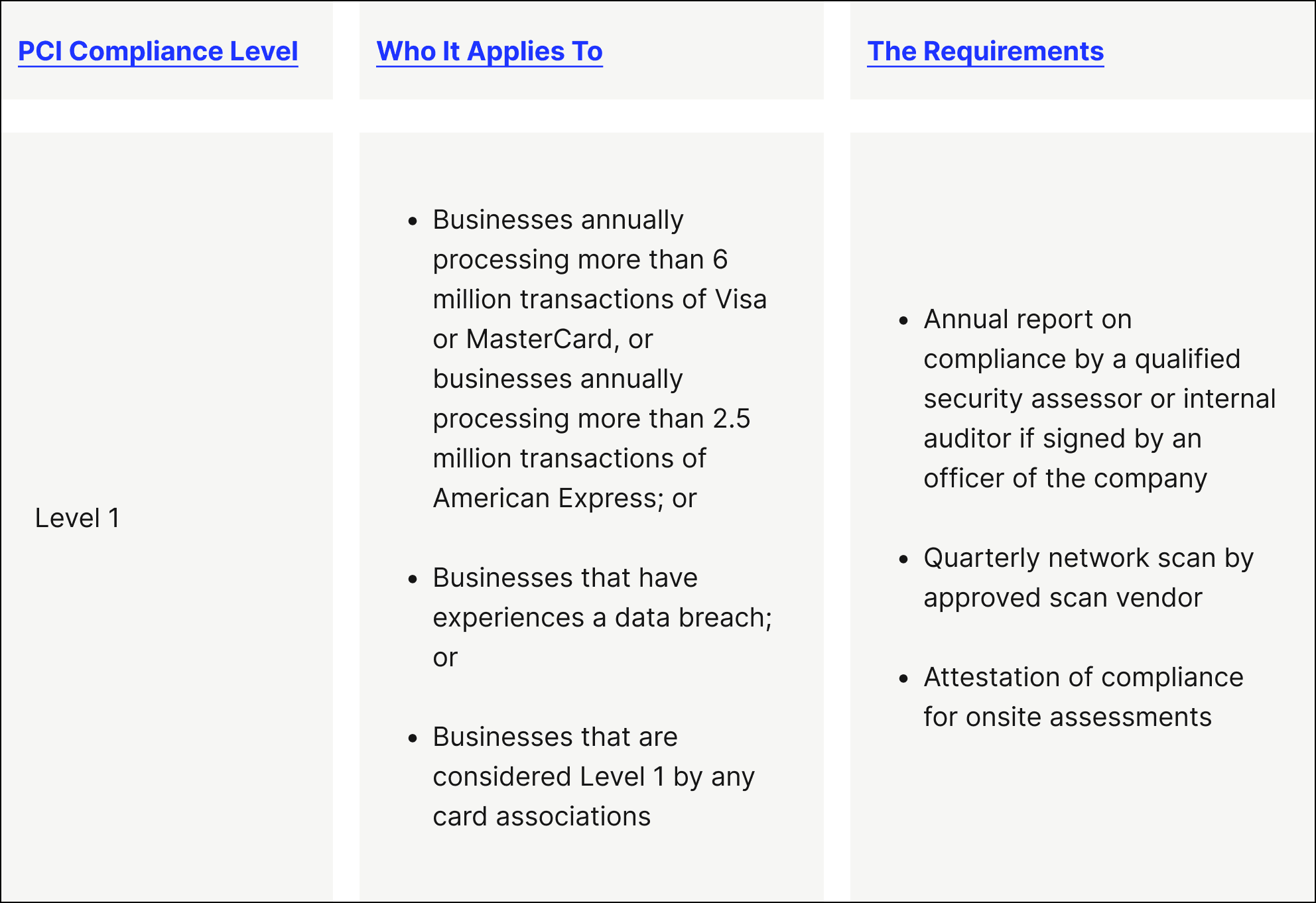
- PCI level 1 — This is the highest level of PCI compliance security requirements, intended for merchants that process over 6 million credit card transactions every year.
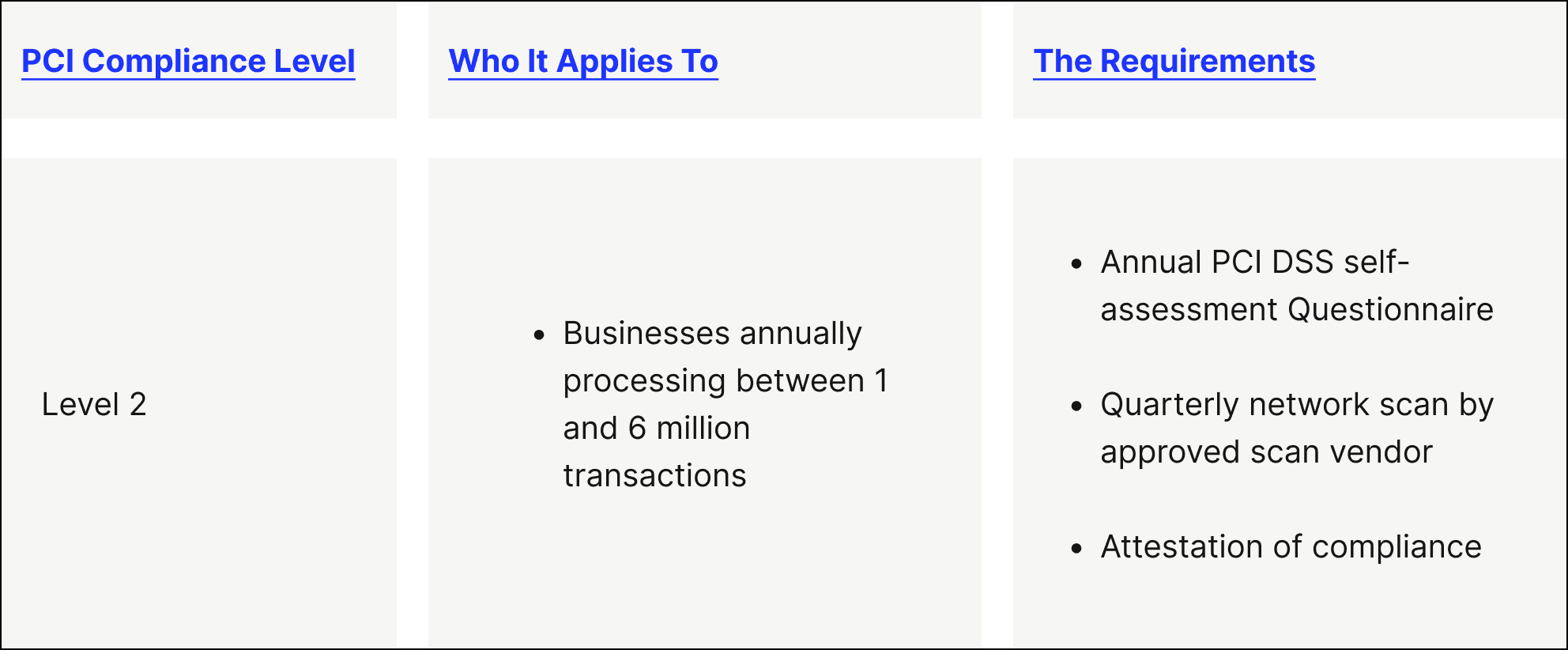
- PCI level 2 — This PCI compliance level is intended for merchants that process between 1 and 6 million credit card transactions every year.
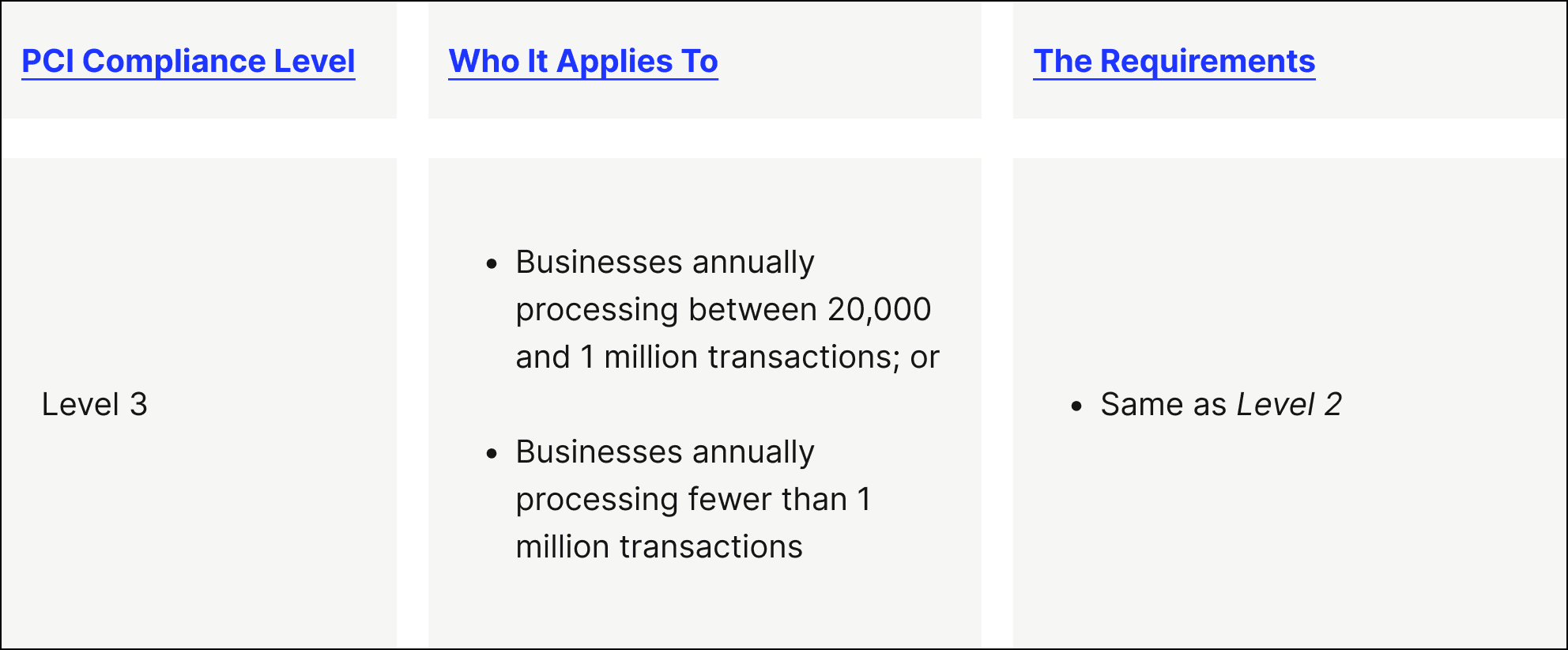
- PCI level 3 — This PCI compliance level is intended for merchants that process between 20,000 and 1 million e-commerce transactions every year.
- PCI level 4 — This PCI compliance level is intended for merchants that process fewer than 20,000 e-commerce transactions or up to 1 million total transactions (regardless of the payment acceptance channel) yearly.
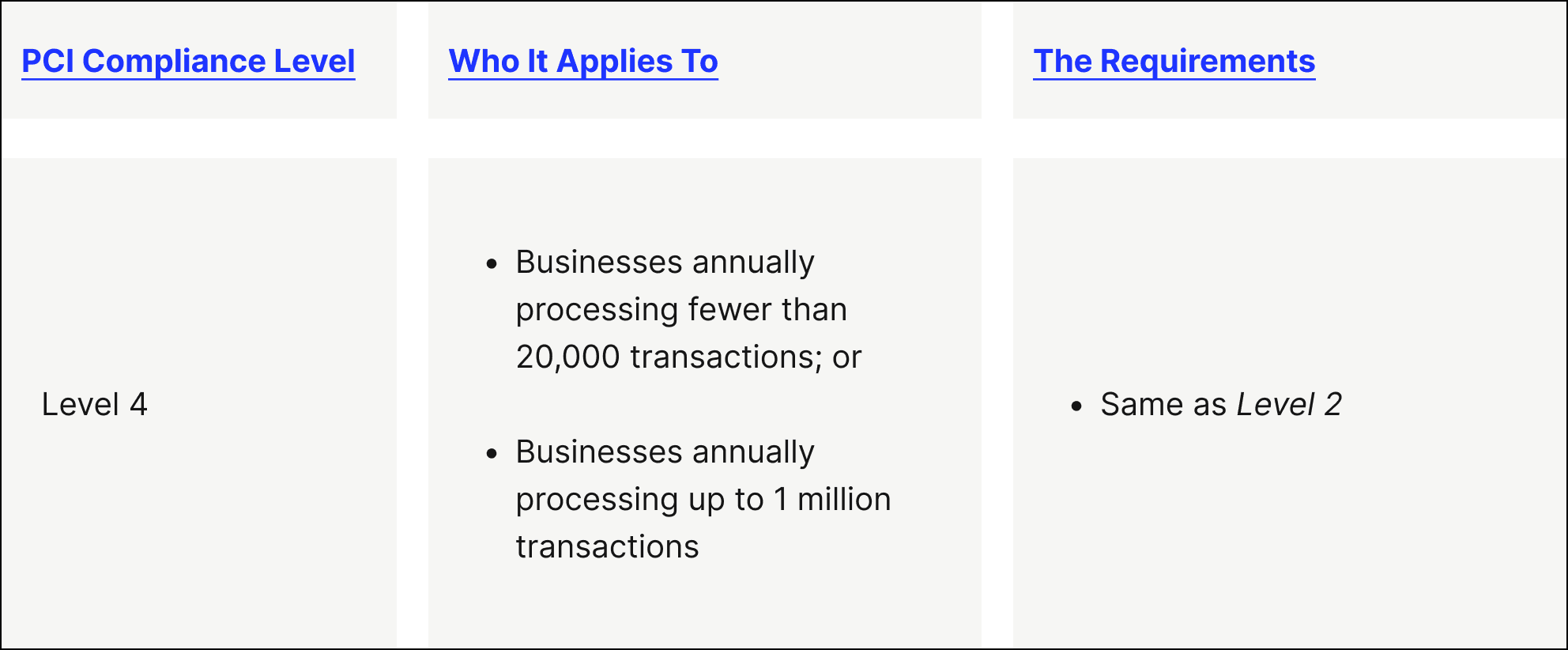
More advice about PCI compliance levels:
If a merchant experiences a data breach that results in account data being compromised, they may have to adhere to a higher level of PCI compliance security requirements, regardless of how many card transactions they process.
Merchants within Level 1 must be assessed by a third party to be considered PCI compliant (through what’s known as a Qualified Security Assessor), while merchants in Levels 2 to 4 can self-evaluate their PCI compliance through a Self-Assessment Questionnaire (SAQ)
To validate that your business is PCI compliant, you’ll need to fill out an SAQ every year. The specific SAQ form you complete will depend on the environment you accept credit cards in—face-to-face, e-commerce, or by mail or telephone (also known as “card-not-present”)—and the method used to send the information (e.g., via the internet or not). For every payment environment you support, you’ll fill out a separate SAQ. To receive a passing mark for PCI compliance means you’ve met 100% of the criteria outlined in your respective SAQ.
For the most up-to-date PCI compliance information for individual card networks, click on your preferred card brand: Visa, Mastercard, American Express.
What are the PCI DSS self-assessment questionnaires?
There are nine different SAQ forms. If you want to be PCI compliant, you’ll need to fill out a separate form for every payment integration method:
1. SAQ A — You’ll fill out this form if you accept payments through card-not-present (e-commerce or mail telephone order), where you outsource all cardholder data functions to a secure third party and you don’t store, process, or send cardholder data on your systems or premises.
2. SAQ A-EP — You’ll fill out this form if you accept payments through e-commerce channels, where your website doesn’t directly receive cardholder data, you outsource all payment processing to a secure third party, and you don’t store, process, or send cardholder data on your systems or premises.
3. SAQ B — You’ll fill out this form if you accept payments through imprint machines and/or card reader terminals that send data through a phone line and don’t store cardholder data.
4. SAQ B-IP — You’ll fill out this form if you accept payments through an internet-based standalone card reader terminal (not connected to other devices on the network) that doesn’t store cardholder data.
5. SAQ C-VT — You’ll fill out this form if you accept payments by entering a single transaction at a time manually or through a secure virtual terminal solution and you don’t electronically store cardholder data.
6. SAQ C — You’ll fill out this form if you accept payments through a payment application system connected to the internet (does not include e-commerce) installed on a computer and any accompanying devices like card readers and you don’t electronically store cardholder data.
7. SAQ P2PE-HW — You’ll fill out this form if you accept payments through a hardware payment terminal included in a PCI-validated solution with point-to-point encryption (P2PE) that doesn’t store cardholder data.
8. SAQ D (for Merchants) — You’ll fill out this form if you accept payments through a method not listed in the descriptions above.
9. SAQ D (for Service Providers) — You’ll fill out this form if you’re a service provider eligible to complete an SAQ.
How to become PCI compliant?
PCI compliance should be an ongoing effort year-round, beyond the annual PCI compliance certification. Even if your security measures passed an evaluation, if these are not continuously monitored, they could be out of compliance by the time your business is the target of a breach.
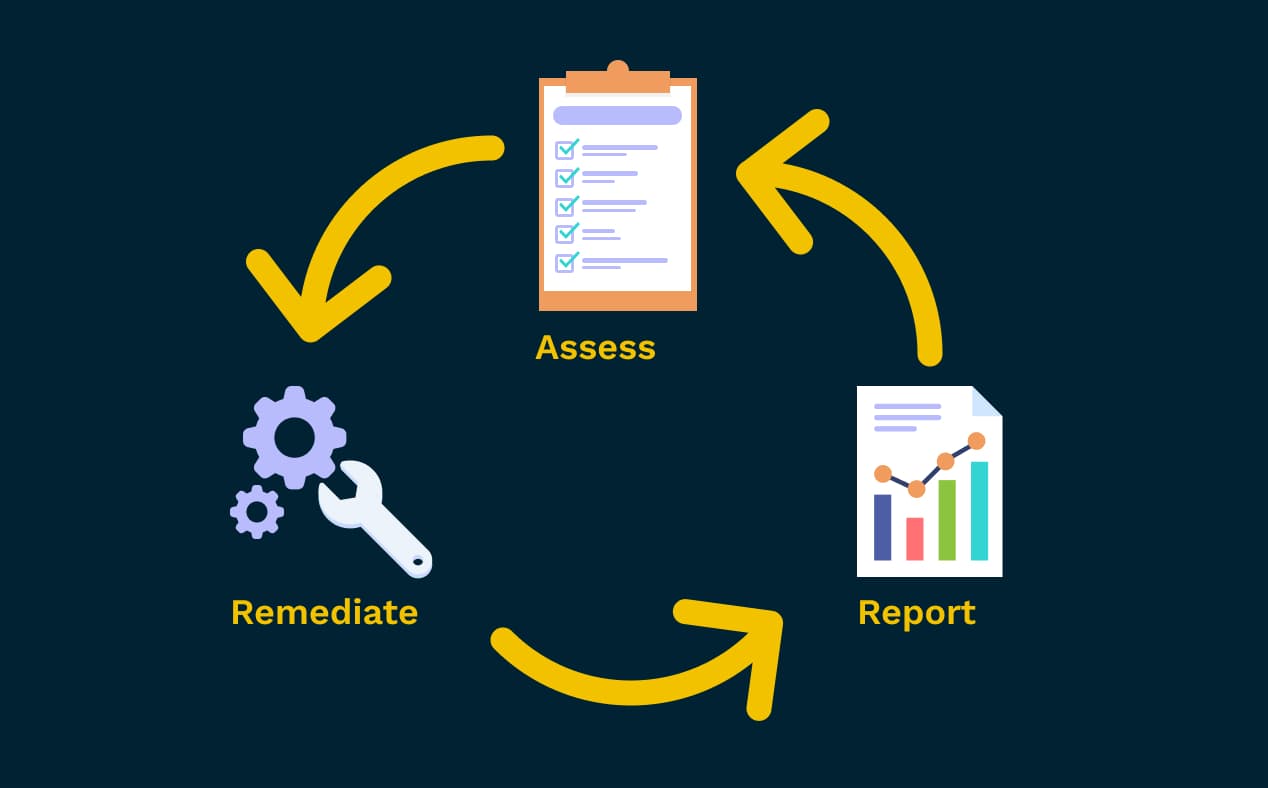
To assess and maintain payment security compliance is to ensure continuous effort. The PCI SSC describes PCI compliance as an ongoing three-step process:
1) PCI compliance step 1: Assess — Before your annual assessment, start by taking inventory of all your business’ IT systems and processes involved in handling card data or sensitive authentication data, looking for any potential vulnerabilities. You’ll want to document all the people, systems, and processes in scope for PCI compliance.
2) PCI compliance step 2: Remediate — When you discover vulnerabilities, you’ll want to address them right away—don’t wait until it’s too late. Only store cardholder data if it’s necessary, and in that event, take essential steps to secure that data.
3) PCI compliance step 3: Report — Diligently compile the required reports—either a Report on Compliance or a Self-Assessment Questionnaire, depending on the nature of your business and how you accept and process card payments—and submit them to the proper acquiring banks and card brands.
What are the 12 PCI DSS requirements?
(Note that the ‘PCI DSS Requirements’ copy in the images below is taken from ‘Version 4.0’ of the ‘PCI DSS Requirements and Testing Procedures’.)
The PCI Data Security Standards cover 12 requirements that must be followed by any business that accepts or processes credit card payments. The PCI SSC groups these requirements into six unique buckets—or goals:
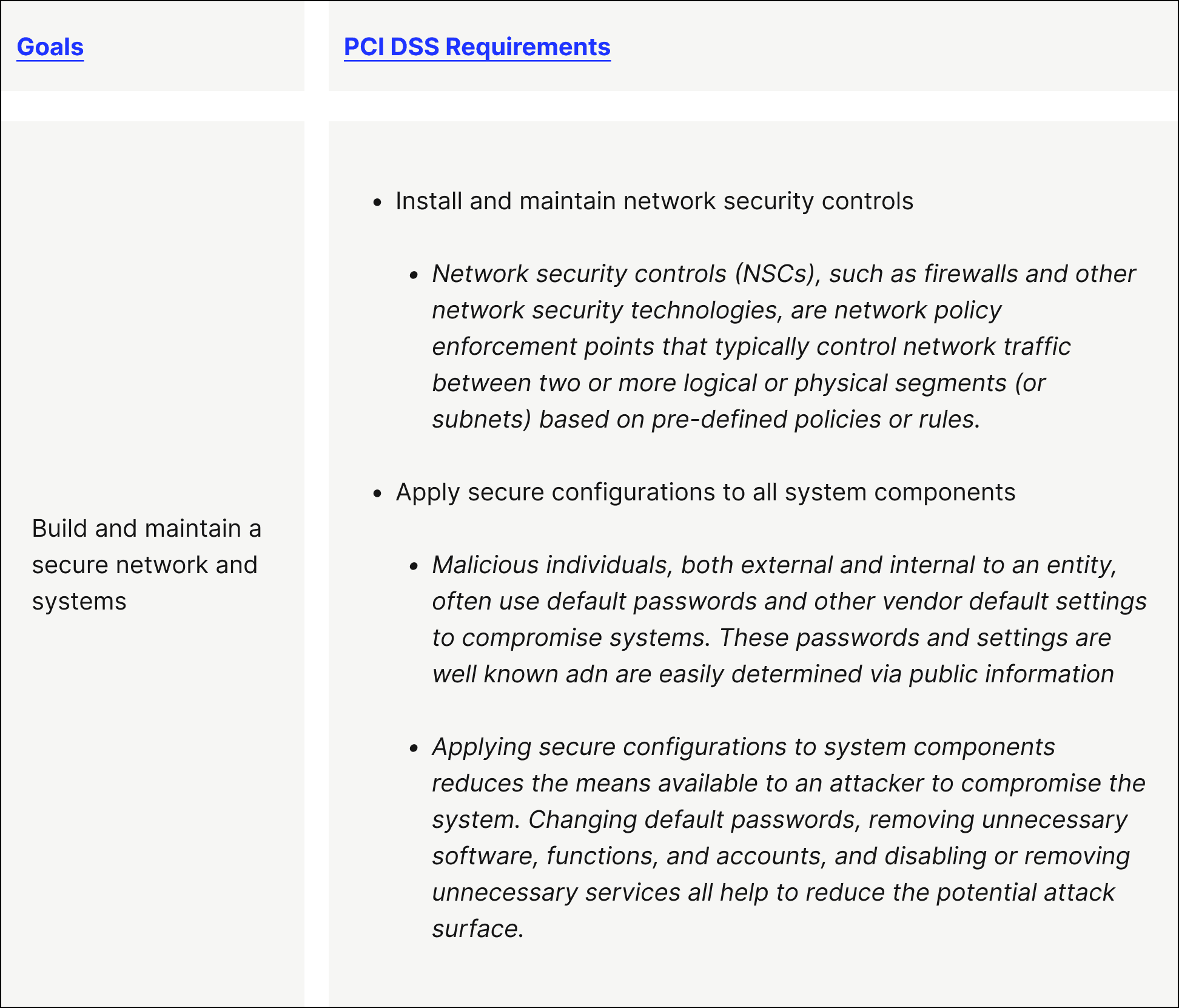
Goal 1. Build and maintain a secure network and systems
PCI DSS Requirement 1 — Install and maintain network security controls
PCI DSS Requirement 2 — Apply secure configurations to all system components
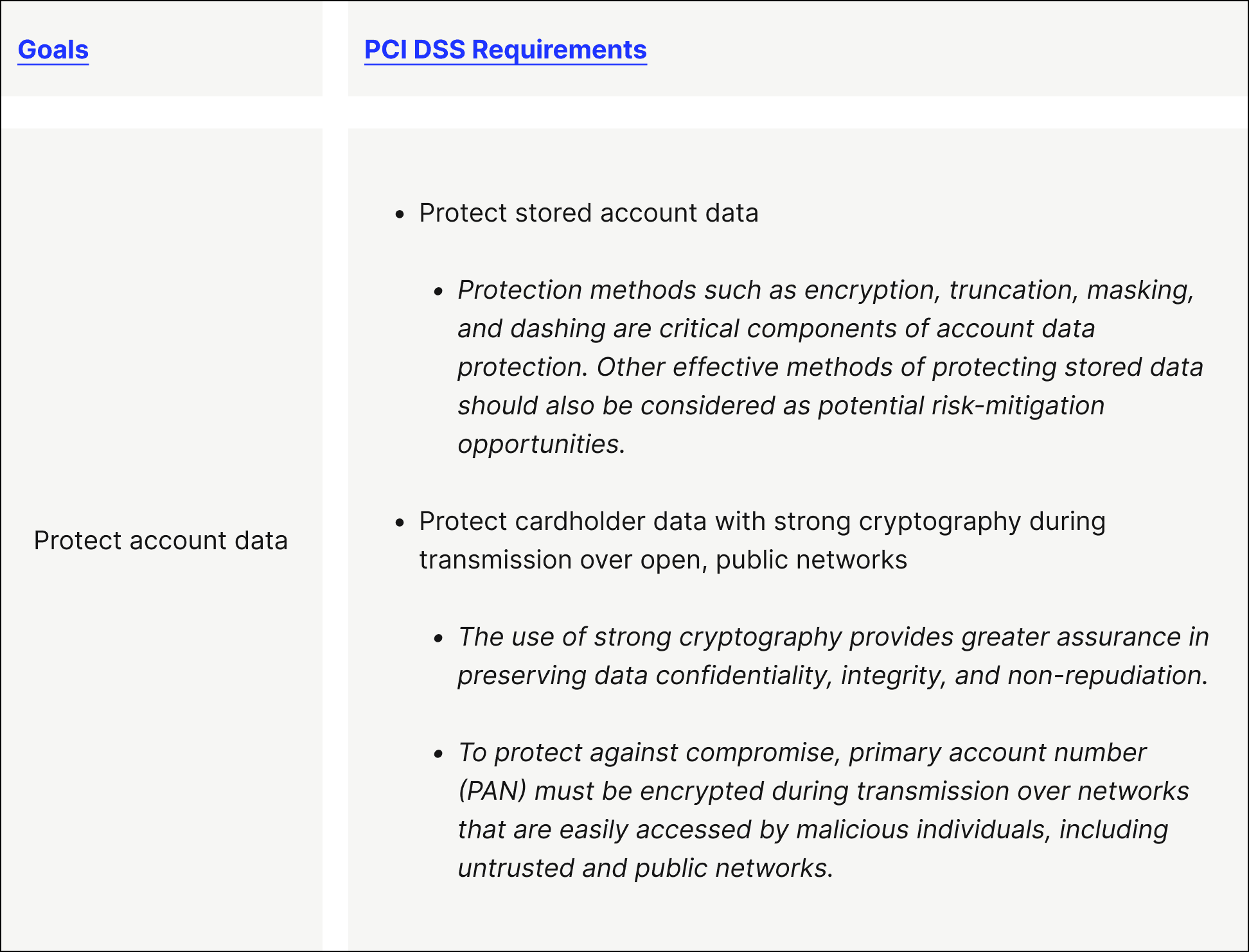
Goal 2. Protect account data
PCI DSS Requirement 3 — Protect stored account data
PCI DSS Requirement 4 — Protect cardholder data with strong cryptography during transmission over open, public networks
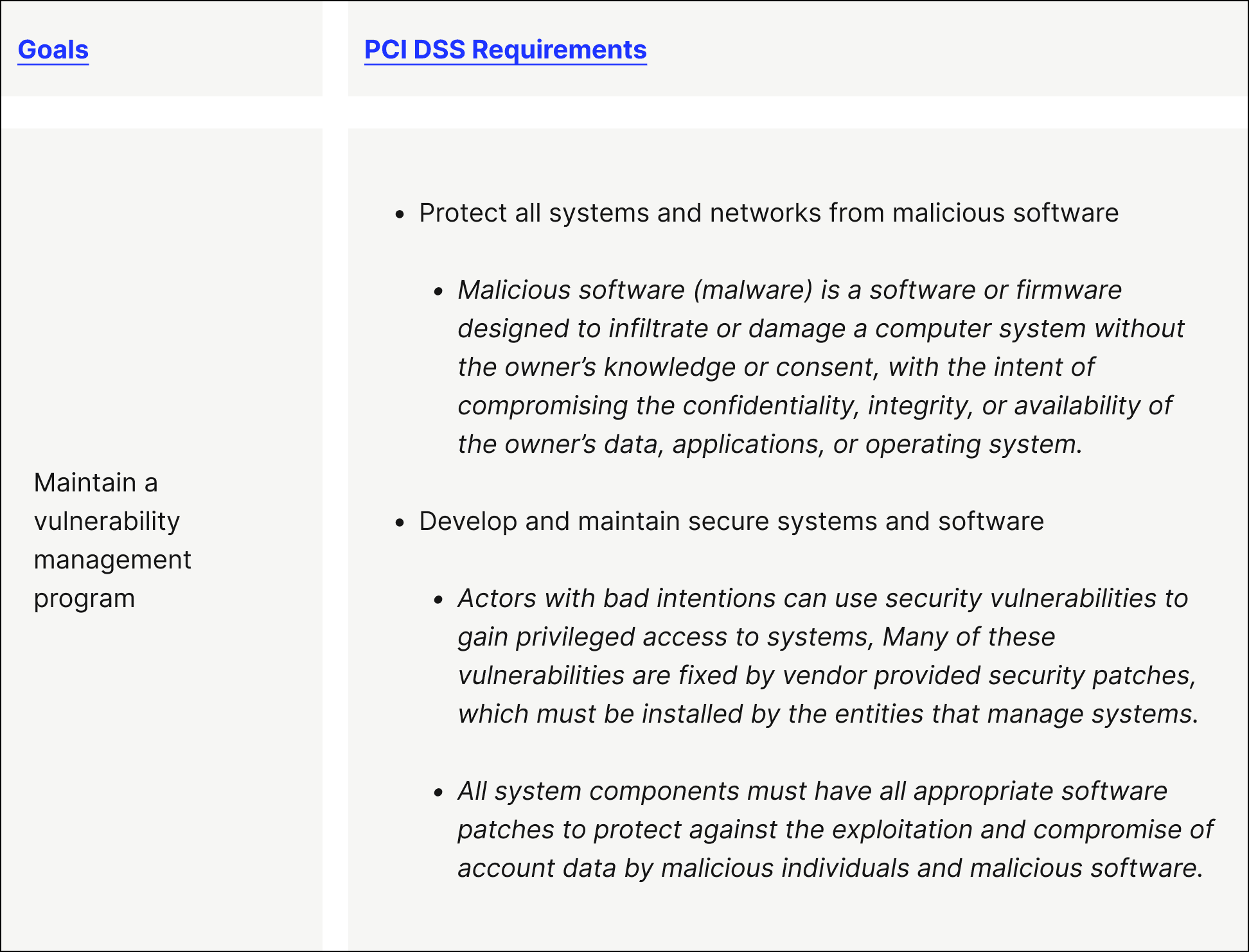
Goal 3. Maintain a vulnerability management program
PCI DSS Requirement 5 — Protect all systems and networks from malicious software
PCI DSS Requirement 6 — Develop and maintain secure systems and software
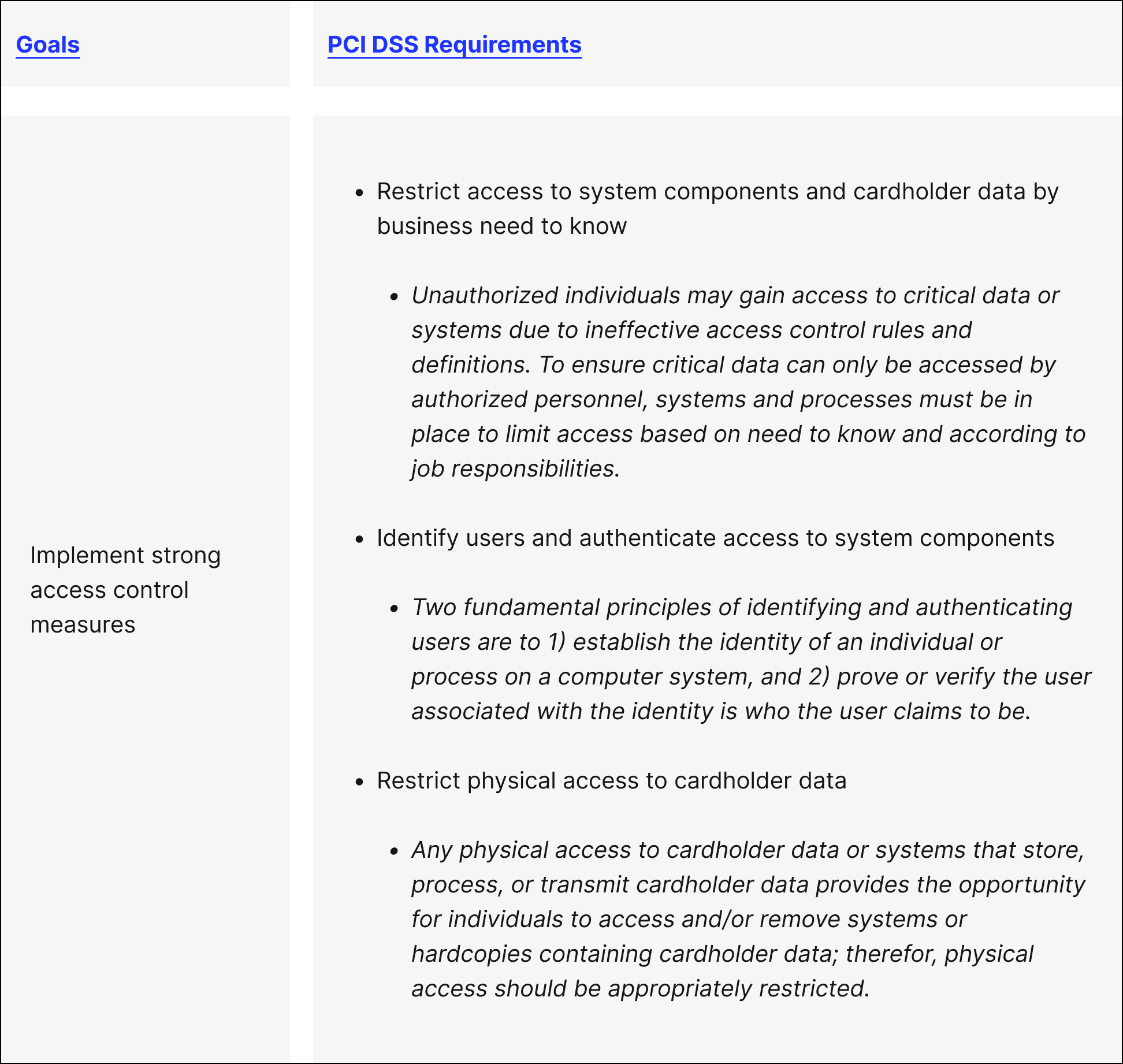
Goal 4. Implement strong access control measures
PCI DSS Requirement 7 — Restrict access to system components and cardholder data by business need to know
PCI DSS Requirement 8 — Identify users and authenticate access to system components
PCI DSS Requirement 9 — Restrict physical access to cardholder data
Goal 5. Regularly monitor and test networks
PCI DSS Requirement 10 — Log and monitor all access to system components and cardholder data
PCI DSS Requirement 11 — Test security of systems and networks regularly

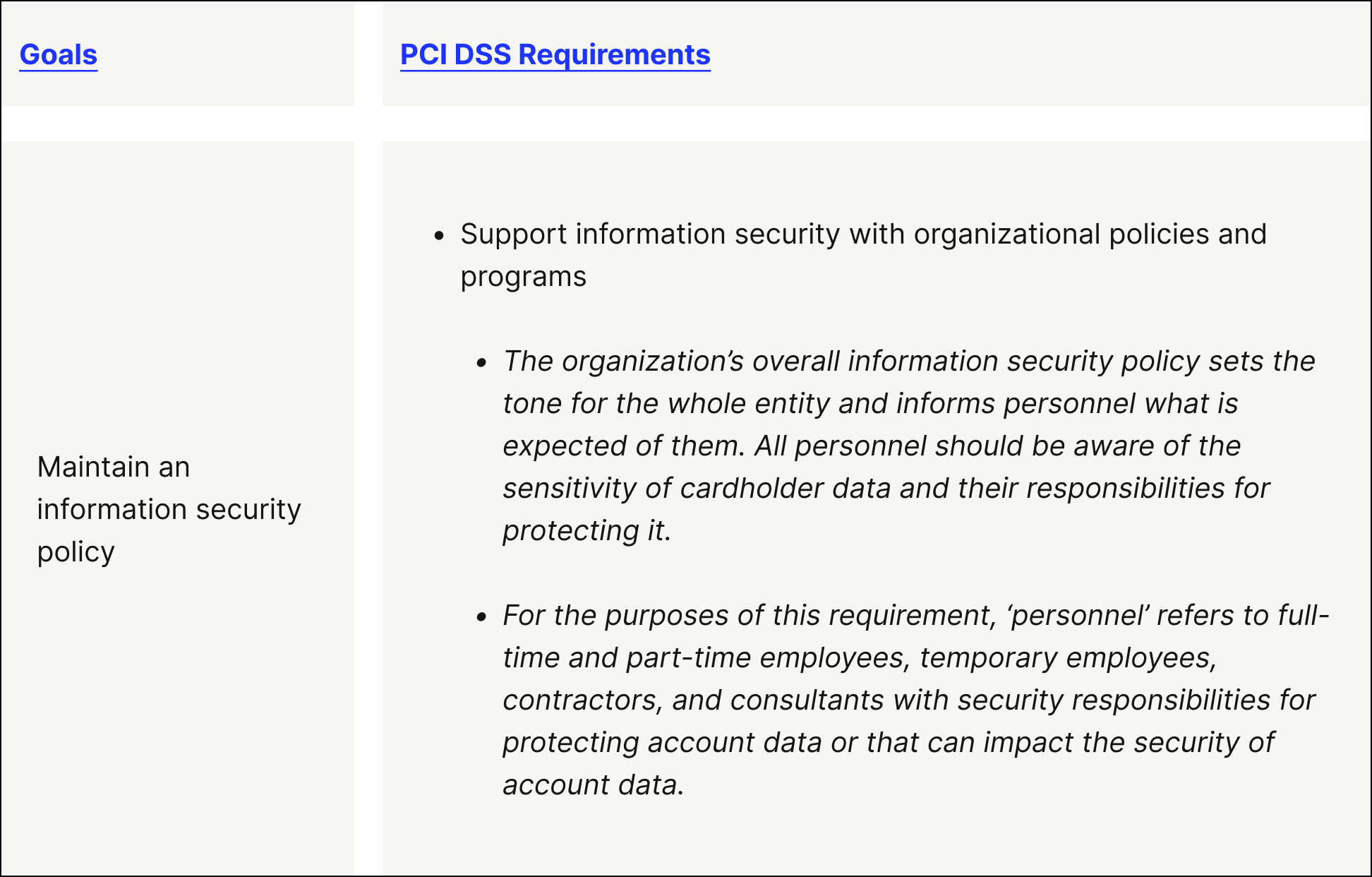
Goal 6. Maintain an information security policy
- PCI DSS Requirement 12 — Support information security with organizational policies and programs
What are the risks of not adhering to PCI compliance requirements?
Following a PCI compliance checklist is mandatory if your business accepts credit card transactions. Those found to be PCI non-compliant are subject to fines and penalties and might lose the ability to process future credit card transactions.
That said, Verizon Cyber Security Consulting suggests—in their 2023 Payment Security Report—not hastily implementing PCI security requirements in the shortest possible time. This often leads to a ‘checkbox’ approach, which …”might not result in producing a truly effective control environment.”
While being PCI compliant doesn’t guarantee immunity from security incidents, there’s data that demonstrates compliance playing an integral role in preventing data breaches. While Verizon’s most recent study doesn’t include updated numbers, their 2020 study found that 53% of businesses that experienced payment data breaches (over a 6 year period spanning the late 2010s) were PCI non-compliant (they found that 0% of compliant businesses experienced a breach). .
The costs of falling victim to a data breach can be considerable. If a breach involving stolen credit card information is traced back to your business, then you’re on the hook for any fines and fees associated with it (such as covering the losses and card replacement costs). But beyond opening your business up to the potential for data breaches and the accompanying financial losses (not to mention the cost of mitigation efforts and lost sales), not meeting PCI compliance requirements can also mean:
Losing customers’ trust—especially in case of a security breach. And the impact of customer experience on B2B payments is profound.
Losing out on potential partnerships, as payment brands want to collaborate with companies that exemplify a commitment to security.
Damaging your brand’s reputation.
Negatively impacting buyers’ credit.
While keeping your PCI compliance status up to date requires ongoing effort and prioritization from your team, the resulting protections for your business and your customers are indisputable.
Why should you partner with a secure ERP-embedded payment processor?
When you use a secure payment processor that can integrate directly with your enterprise resource planning (ERP) system, you’re able to minimize your team’s contact with sensitive payment information even further, as it’s tokenized and recorded automatically, without any manual intervention.
Versapay’s payment processing software integrates natively with leading ERPs like:
This lets you accept payments from a variety of channels like e-commerce, point of sale, card-not-present, and over the phone. Versapay encrypts and tokenizes all payments across all channels, ensuring the data never touches your servers.
Versapay’s dedicated support team also works with you to ensure you’re following security best practices, offering their seasoned expertise to help you put controls in place to minimize potential impacts of fraudulent activity.
In the global effort to prevent security breaches and data theft, PCI compliance is just the beginning. Investing in security—in and out of the payment environment—as a business-wide priority will help you protect your business and your customers in the long-term.
Want to deepen your understanding of the credit card processing lifecycle? Check out The Ultimate Guide to Credit Card Processing to learn exactly how credit card transactions are processed, understand the fees involved, and get tips for finding the best deal when looking for a payment processing solution.
Frequently asked questions about PCI compliance
1. What are the benefits of PCI compliance?
Being PCI compliant means being vigilant and ensuring there are no security gaps. This helps avoid theft of sensitive cardholder information, like social security numbers, driver’s license numbers, health information, etc.
PCI compliance is the industry standard, too, and those found to be non-compliant face substantial fines for violating the agreement and being negligent. Non-compliance leaves businesses vulnerable to payment—and other—fraud, data breaches, and theft.
2. Who must be PCI compliant?
If you generate revenue from debit, credit, prepaid—or any other type of—cards, then you must be PCI compliant. PCI compliance applies to all entities storing, processing, and/or transmitting cardholder data.
3. What are the PCI DSS compliance levels?
There are 4 PCI compliance levels: Level 1, Level 2, Level 3, and Level 4. The PCI compliance requirements per level vary based on factors like credit card transaction volume processed annually.
4. Is there a PCI non-compliance fee?
Yes, there is a PCI non-compliance fee. They begin at $5,000.00 but can grow to $500,000.00 per incident. Additionally, businesses having compromised information must inform those affected individuals—in writing—that fraudulent charges might occur.
5. What does PCI DSS stand for?
PCI DSS stands for PCI Data Security Standards. These are the rules established to govern how businesses manage cardholder data to ensure secure payment processing.
About the author

Jordan Zenko
Jordan Zenko is the Senior Content Marketing Manager at Versapay. A self-proclaimed storyteller, he authors in-depth content that educates and inspires accounts receivable and finance professionals on ways to transform their businesses. Jordan's leap to fintech comes after 5 years in business intelligence and data analytics.