The Most (and Least) Secure Payment Methods in B2B
- 11 min read
The potential for fraud can dissuade some businesses from making the jump to accepting digital payments. But, there are compelling reasons not to let payment fraud be a deterrent. We’d argue that now, more so than ever, is the best time to embrace digital payments.

Cybercrime is on the rise—we won’t skirt around that fact. There were 4.7 million identity theft and fraud reports in the US in 2020 alone, up 45% from the year prior. And card fraud losses are expected to jump to $38.50 billion by 2027.
These numbers aren’t insignificant but choosing not to accept online payment methods will have you at such an arguably greater disadvantage. Your competitors will have surpassed you long before you even consider enacting digital transformation.
Here are some quick statistics that prove why B2B businesses should be accepting digital payment methods:
- Opportunities for greater revenues. Offering multiple payment options can increase revenue by nearly 30%
- Increasing willingness to buy online. 70 to 80% of B2B decision makers prefer remote human interactions or digital self-serve
- Changing payment habits. 60% of financial professionals are likely to convert most of their payments to suppliers from checks to electronic payments
These numbers hardly tell the entire story. But with the way things are going, businesses who choose not to support digital payments will find themselves on the outside, looking in.
To provide payment experiences that are on par with those in the business-to-consumer (B2C) world—which customers increasingly expect—business-to-business (B2B) sellers need to understand the payment methods at their disposal, and which are most advantageous for themselves and their customers.
We've compiled a list of the most—and the least—secure payment methods. Notice anything? (Hint, hint. The most secure are all digital payment methods.) We’ve also included tips for making digital payments even more secure.
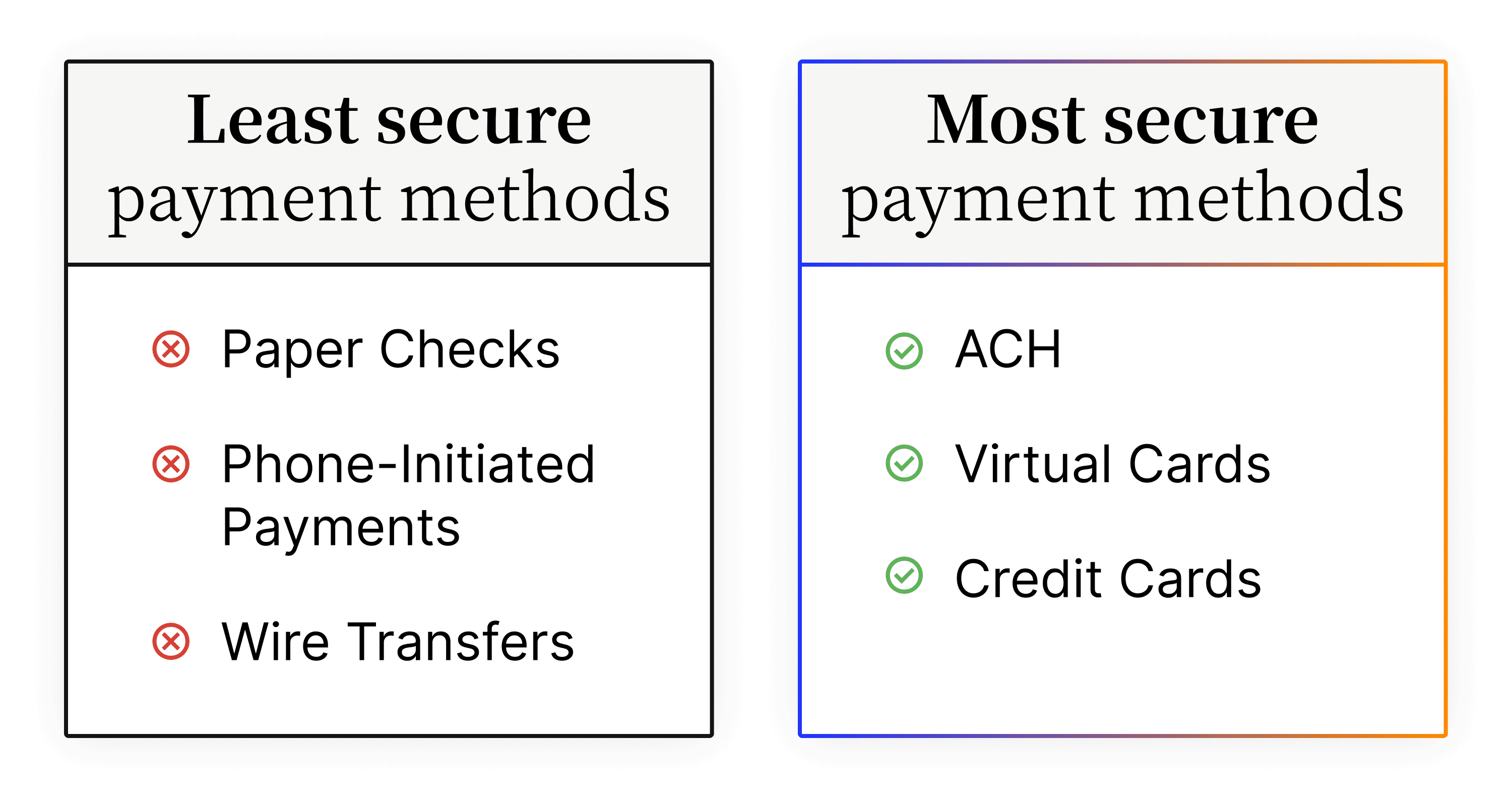
The most secure payment methods
1. ACH
What are ACH payments?
An ACH payment is an electronic transfer of funds run by the National Automated Clearing House Association (NACHA) in the United States. With an ACH payment, funds move electronically from one bank to another through the ACH network. This network connects every single US financial institution. It gives them the ability to transfer money from one bank to another safely, quickly, and securely.
Why are ACH payments secure?
ACH payments are increasingly popular—the total volume of payments made on the ACH network in the third quarter of 2021 was 7.3 billion (totaling $18.1 trillion in value), up 7.7% from the second quarter, which was already up 9.9% over the first quarter.
The reason for this growth (particularly in B2B, which accounted for 1.4 billion of the transactions made in Q3 of 2021) is because ACH is generally considered the most secure payment method between businesses.
ACH payments go through a clearinghouse that keeps account numbers confidential (while enforcing its own rules and regulations). The Electronic Fund Transfer Act, enacted in 1978, serves to protect customers who transfer funds electronically and gives them the same confidence they have (but maybe shouldn’t) in the checking system. Among other things, this Act gives sellers and buyers a 60-day period to recover funds lost to fraud or error.
ACH payments are not exempt from fraud, however, as employees often still have access to sensitive information. But with the other safety measures that exist, buyers and sellers can be more confident in the security of these transactions.
2. Virtual cards
What are virtual cards?
Virtual cards are single-use credit card numbers that are generated for each vendor payment. As the name suggests, they are entirely virtual—no plastic, no chips, no PINs. Buyers typically enjoy using virtual cards as they offer improved security, better control, and complete transaction details. Sellers are increasingly beginning to embrace this payment method, as secure payment systems are cropping up that provide straight-through-processing for virtual cards and integrate with their enterprise resource planning (ERP) systems to input remittance data automatically.
Why are virtual cards secure?
Virtual cards are nearly impossible to defraud. There are a few reasons for this:
- Virtual cards have a limited shelf-life, meaning they’re only valid for a limited period or for a limited number of transactions—in many cases, just one.
- Virtual cards ensure that any sensitive credit card details (on the buyer’s primary credit card) are not shared with you when accepting the payment.
- Even if a virtual card number is compromised, the buyer’s actual account number will be masked.
B2B payments often require some manual lift when facilitating transactions. With this comes the risk of human error. Virtual cards—and their single use nature—can eliminate this risk entirely. B2B buyers can rest assured knowing a virtual card was used for its intended purpose, and account information was not transferred through numerous parties before a payment was completed.
3. Credit cards
What are credit cards?
A credit is an agreement between lenders and borrowers. Borrowers—often the customer or buyer—receive sums of money from lenders to pay for goods or services. That money must be repaid to the lender later—often with interest. This is the biggest difference between payments made with debit cards and credit cards. Payments made with credit cards are not deducted right away, instead going on the buyer's line of credit, indicating that the funds will be paid later.
Why are credit cards secure?
Despite how rampant payment fraud has become—and despite credit cards seemingly being at the center of so many fraudulent attacks—credit cards are still one of the three most secure payment methods. This is especially the case for B2B buyers.
Credit cards aren’t linked to buyers’ bank accounts—instead, the card issuer (Visa, Mastercard, American Express, etc.) will be paying each transaction (that is, until the bill needs paying, of course!). Other alternative digital payment methods—like debit cards or electronic checks—are linked directly to customer accounts. In the event these methods are compromised, fraudsters would gain access to all funds stored in an account.
When using credit cards, buyers can pay securely and more easily be made aware of fraudulent attacks. Technology has enabled card issuers to notify cardholders of any suspicious activities or transactions that might be indicative of their card being compromised.
Many card issuers make it so that their cardholders can lock their credit cards—both their physical and virtual varieties—at the tap of a button, ensuring they clamp down on fraud within moments of it being identified. And those fraudulent transactions that make it through? Card issuers have the power to freeze any credit card transactions that are in dispute, meaning the buyer will only need to pay for it once the dispute (also known as a chargeback) is resolved, and if it's ruled in their favor, then not at all.
Lastly—and this is particularly notable in B2B—there are smart corporate credit cards that can introduce further security measures. These cards often come with robust controls that block unapproved spending.
The least secure payment methods
1. Paper checks
What are paper checks?
A paper check is a written, dated, and signed document—prepared by the customer or buyer—that directs their bank to pay a specific amount of money to the supplier. While paper check usage is steadily declining, many B2B businesses are still reliant on the payment method.
Why are paper checks not secure?
Paper checks are not a secure form of payment. Yet, in a recent Versapay survey, 91% of tech leaders in their organization’s finance department said they still receive check payments from customers. And while this survey also found that the volume of digital payments respondents receive have increased over the last 12 months, 49% of finance leaders saw an increase in paper checks.
The reason for this increase stems from buyers’ resistance to change deeply ingrained buying and record-keeping habits. For example, one construction executive was quoted saying, “People like the money-in-hand feeling. They feel they have more control over physical checks. They do not trust electronic payments.”
Another retail executive said, in response to a question about why buyers are hesitant to move away from making payments by check, “I think it’s because that’s what they’re used to. They trust what they always rely on.”
Familiarity and a false sense of security are driving check fraud, and it’s time to put those falsehoods to rest. Paper checks include too much sensitive information that when acquired by fraudsters, can have severe implications. In the wrong hands, account and routing numbers, along with contact details, can compromise buyer security and wreak financial havoc.
Beyond the known concerns associated with paper checks, fraud experts are sounding the alarm on why checks are insecure payment methods. Steve Kenneally, Senior Vice President of Payments and Cybersecurity Policy for the American Bankers Association boils it down to two sentences: “What you’re doing is handing someone a piece of paper with your name, address and bank account information. Electronic payments, by contrast, are safer, faster, and cheaper.”
2. Wire transfers
What are wire transfers?
The term wire transfer is often used interchangeably with ACH. While the two work very similarly, there are some notable differences that make wire transfers less secure. The two payment methods vary in seven major ways, detailed in the chart below:
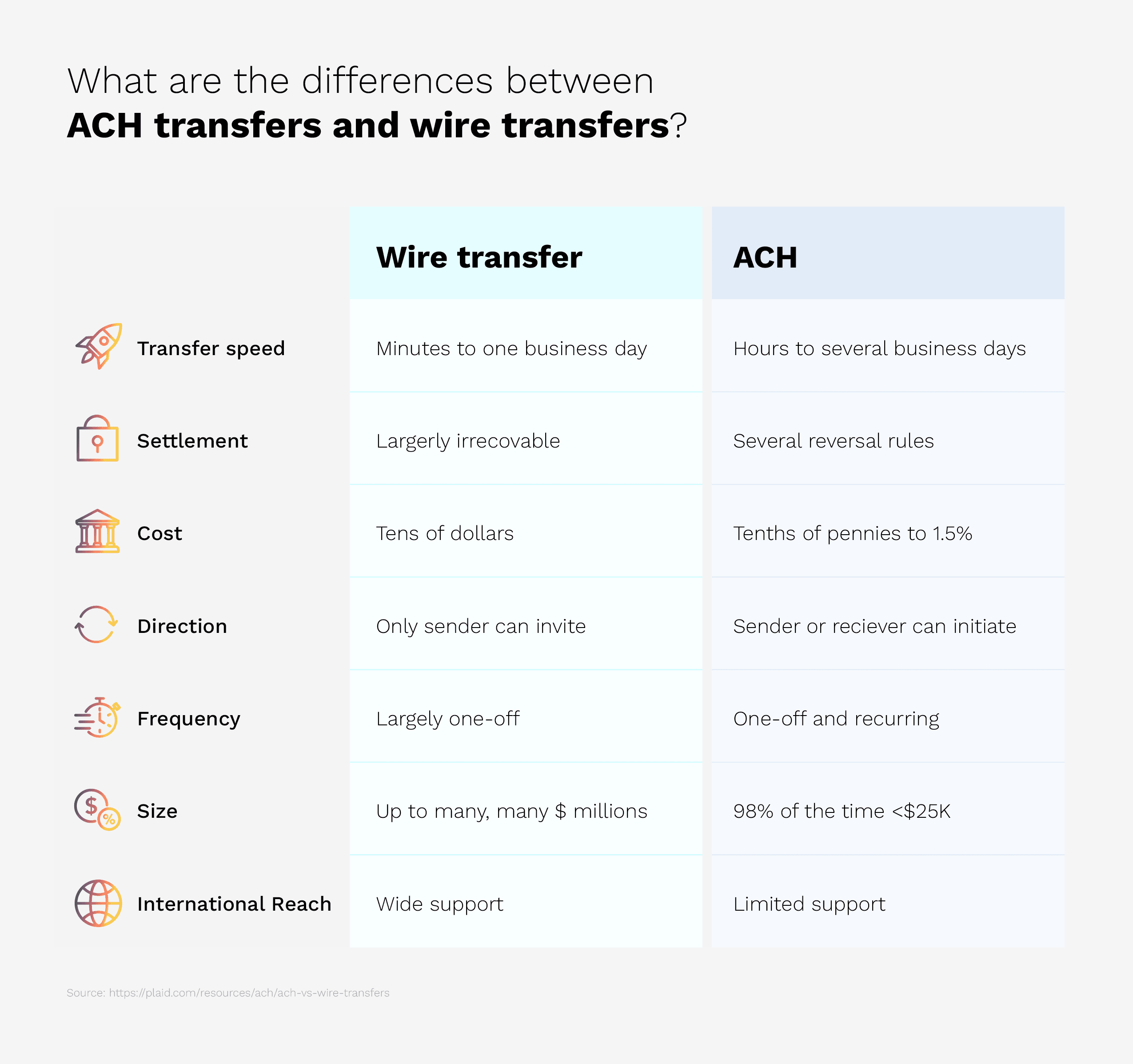
Why are wire transfers not secure?
While appealing due to their incredible transfer speed (in as little as minutes) and transaction volume capacity (up to multiple million dollars in a single transfer), wire transfers remain an attractive target for fraudulent activity—for the same very reasons.
Tack on the immediate settlement of the payment—wire transfers cannot be refunded or cancelled once initiated—and the lack of internal controls, and you might as well be rolling out the red carpet for fraudsters if you’re still dealing in wire transfers.
Wire transfer fraud is most commonly the Robin to Business Email Compromise’s (BEC) Batman. BEC happens when fraudsters identify a victim’s behavior and poses as someone whom they trust—a legitimate recipient such as a third-party vendor, for example.
The fraudster will then make an urgent—and completely false—request instructing the victim to immediately wire funds to the payment instructions they provide. Because wire transfers cannot be reversed, it's very difficult to re-acquire the funds your AP department might have transferred to the fraudster’s bank account.
According to the Association for Financial Professionals (AFP), 76% of organizations experienced business email compromise in 2020—a slight increase from 75% in 2019—and wire transfers were the highest targeted payment methods of those attacks, accounting for 43% of them.
Wire transfers are also expensive to initiate! So, if you’re not convinced of their security vulnerabilities, maybe the $25 to $50 in bank fees per wire transfer might have you seeing otherwise.
3. Phone-initiated payments (card-not-present)
What are card-not-present transactions?
A card-not-present (CNP) transaction most commonly occurs when the cardholder and credit card are not physically present at the time of the transaction. This payment method is most prevalent when transactions occur over the phone, by fax, internet, or mail.
There are many different types of CNP transactions, some more common than others. These include online purchases, phone-initiated payments, recurring payments, online invoice payments, and card-on-file payments. The least secure of these—and the least secure of all payment methods—are phone-initiated payments.
Why are phone-initiated (card-not present) transactions not secure?
When payment options are limited, some businesses resort to accepting credit card payments for invoices over the phone. This process is highly manual, and for businesses looking to maintain a secure payment environment, is not great for ensuring PCI compliance. The goal of the PCI DSS is to minimize the scope of the cardholder data environment. This means that the people, processes, and technologies that store, process, or transmit credit card information should be pared down to only those most vital to facilitating transactions.
Phone-initiated payments put B2B sellers firmly in PCI DSS scope. What’s more, the actual effort of processing payments over the phone is sluggish, inefficient, and error prone. Credit card information relayed over the phone is not tokenized, forcing humans to interact with and handle sensitive card data. That data must often be destroyed (for instance if it was recorded on a piece of paper) after it was appropriately inputted into your accounting systems.
Complications from phone-initiated payments may also arise before a transaction is even facilitated. When transactions are performed over the phone, it can be difficult for merchants to verify the identity of the buyer, often forcing them to work rigorously to prove it. Common protections to lessen these risks and verify identity—such as signatures and encrypted card chips—simply do not work in dealings over the phone.
How do you make digital payments even more secure?
Many third-party providers are often involved in processing secure payments online. You’ve got your payment processors, your payment gateways, your merchant acquirers, your issuing banks, and your ERPs—among many others. The more hands a digital payment passes through, the more vulnerabilities exist. And a fraudster could use any one of those vulnerabilities as an access point.
The digital payment ecosystem is fragmented. Whether it's B2C to B2B, businesses are engaging with multiple third-party service providers and weaving their solutions into their own internal information technology infrastructure. Understanding the full landscape of that ecosystem is critical for businesses looking to prevent payment fraud
There are numerous brute force methods merchants and suppliers can implement for secure online payments—such as introducing CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart)—at their online shopping carts to heighten payment security and reduce payment fraud. One of the best ways to maximize online payment security is to partner with an integrated payments solution embedded seamlessly with your ERP. This eliminates many of the vulnerabilities that arise from handoffs between third-party providers.
These integrated payments solutions can allow buyers to securely store their payment information, too. This enables them to more easily store funds, make purchases, and track payment history. They make the B2B buyer’s experience significantly more convenient—and most importantly, more secure.
Remember, fraud is usually carried out by bad actors. They use what’s publicly accessible, such as an ecommerce site or a non-gated web-based payment page. Instances of fraud on integrated payments solutions are exceptionally low as buyers often pay through secure portals where logins are required.
Fraud should not prevent you from accepting digital payment methods. Instead, you should embrace digital payment methods as a means of distancing yourself from the potentially devastating impact of falling victim to fraud from traditional payment methods—namely paper checks, wire transfers, and phone-initiated payments.
The most secure payment methods are digital. Download our ebook—Payment Fraud Explained: How B2B Merchants Can Fight Fraud and Maximize Customer Experience—to learn how you can accept and process secured payments digitally using Versapay and significantly minimize your risk of fraud at the same time.
About the author

Jordan Zenko
Jordan Zenko is the Senior Content Marketing Manager at Versapay. A self-proclaimed storyteller, he authors in-depth content that educates and inspires accounts receivable and finance professionals on ways to transform their businesses. Jordan's leap to fintech comes after 5 years in business intelligence and data analytics.